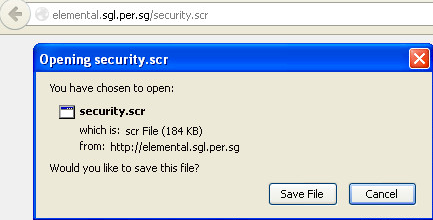
Example of trojan horse attack new arrivals
Example of trojan horse attack new arrivals, Personal Protection Against the Trojan Horse All About Trojan new arrivals
$94.00
SAVE 50% OFF
$47.00
$0 today, followed by 3 monthly payments of $15.67, interest free. Read More
Example of trojan horse attack new arrivals
Personal Protection Against the Trojan Horse All About Trojan
What is Trojan Horse Malware and how can you avoid it
Placeholder Trojan Writing a Malware Software
Trojan Horse Meaning Examples Prevention
No money but Pony From a mail to a trojan horse Malwarebytes Labs
What is a Trojan Horse Virus Definition Examples Removal Options Video
Description
Product code: Example of trojan horse attack new arrivals
What is a Trojan Horse Virus Types Prevention in 2024 new arrivals, Trojan Horse Virus Examples How to Defend Yourself new arrivals, Trojan Horse Meaning Examples Prevention new arrivals, The Infamous Trojan Horse Virus What it is What it does Web new arrivals, What is a Trojan Virus Trojan Horse Malware Imperva new arrivals, What Is a Trojan Horse in Computer Terms InfoSec Insights new arrivals, Trojan Horse your ict clubs new arrivals, What Is a Trojan a Virus or Malware How Does It Work Avast new arrivals, What Is a Trojan Horse in Computer Terms InfoSec Insights new arrivals, What is a Trojan horse attack Shiksha Online new arrivals, Placeholder Trojan Writing a Malware Software new arrivals, Personal Protection Against the Trojan Horse All About Trojan new arrivals, What is Trojan Horse Malware and how can you avoid it new arrivals, Placeholder Trojan Writing a Malware Software new arrivals, Trojan Horse Meaning Examples Prevention new arrivals, No money but Pony From a mail to a trojan horse Malwarebytes Labs new arrivals, What is a Trojan Horse Virus Definition Examples Removal Options Video new arrivals, Malware Based Phishing Attacks 101 What is Malware Phishing new arrivals, What is a Trojan Horse Virus Types Prevention in 2024 new arrivals, What Is a Trojan Horse in Computer Terms InfoSec Insights new arrivals, Different Examples of a Trojan Horse Types of Trojan Horse new arrivals, AIDS Trojan horse Wikipedia new arrivals, Your System Has Been Hacked With A Trojan Virus Email Scam new arrivals, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses new arrivals, What is a Trojan Horse Virus Types and How to Remove it new arrivals, What is Trojan Horse Computing zenarmor new arrivals, My Trojan Captured All Your Private Information Email Scam new arrivals, How to Get Rid of Trojan Horse Virus Trojan horse Itunes Trojan new arrivals, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus new arrivals, How trojan malware is evolving to survive and evade cybersecurity new arrivals, What are Trojan Viruses and How Do These Threats Work Top Cloud new arrivals, What is a Trojan Horse Virus Definition Examples Removal new arrivals, What is a Trojan horse attack Shiksha Online new arrivals, What is a Trojan Horse U.S. News new arrivals, E card spam attack installs Trojan horse CERN Courier new arrivals.
What is a Trojan Horse Virus Types Prevention in 2024 new arrivals, Trojan Horse Virus Examples How to Defend Yourself new arrivals, Trojan Horse Meaning Examples Prevention new arrivals, The Infamous Trojan Horse Virus What it is What it does Web new arrivals, What is a Trojan Virus Trojan Horse Malware Imperva new arrivals, What Is a Trojan Horse in Computer Terms InfoSec Insights new arrivals, Trojan Horse your ict clubs new arrivals, What Is a Trojan a Virus or Malware How Does It Work Avast new arrivals, What Is a Trojan Horse in Computer Terms InfoSec Insights new arrivals, What is a Trojan horse attack Shiksha Online new arrivals, Placeholder Trojan Writing a Malware Software new arrivals, Personal Protection Against the Trojan Horse All About Trojan new arrivals, What is Trojan Horse Malware and how can you avoid it new arrivals, Placeholder Trojan Writing a Malware Software new arrivals, Trojan Horse Meaning Examples Prevention new arrivals, No money but Pony From a mail to a trojan horse Malwarebytes Labs new arrivals, What is a Trojan Horse Virus Definition Examples Removal Options Video new arrivals, Malware Based Phishing Attacks 101 What is Malware Phishing new arrivals, What is a Trojan Horse Virus Types Prevention in 2024 new arrivals, What Is a Trojan Horse in Computer Terms InfoSec Insights new arrivals, Different Examples of a Trojan Horse Types of Trojan Horse new arrivals, AIDS Trojan horse Wikipedia new arrivals, Your System Has Been Hacked With A Trojan Virus Email Scam new arrivals, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses new arrivals, What is a Trojan Horse Virus Types and How to Remove it new arrivals, What is Trojan Horse Computing zenarmor new arrivals, My Trojan Captured All Your Private Information Email Scam new arrivals, How to Get Rid of Trojan Horse Virus Trojan horse Itunes Trojan new arrivals, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus new arrivals, How trojan malware is evolving to survive and evade cybersecurity new arrivals, What are Trojan Viruses and How Do These Threats Work Top Cloud new arrivals, What is a Trojan Horse Virus Definition Examples Removal new arrivals, What is a Trojan horse attack Shiksha Online new arrivals, What is a Trojan Horse U.S. News new arrivals, E card spam attack installs Trojan horse CERN Courier new arrivals.
Example of trojan horse attack new arrivals
- example of trojan horse attack
- examples of electroplated products
- examples of electroplating in industry
- examples of electroplating in daily life
- examples of electroplating objects
- examples of linen
- examples of pumps
- examples of trojan horse virus attacks
- examples of thermometer
- excedrin cooling pads