Backdoor trojan virus new arrivals
Backdoor trojan virus new arrivals, trojans Backdoors Viruses and Worms Pianalytix Build Real new arrivals
$88.00
SAVE 50% OFF
$44.00
$0 today, followed by 3 monthly payments of $14.67, interest free. Read More
Backdoor trojan virus new arrivals
trojans Backdoors Viruses and Worms Pianalytix Build Real
Backdoor Virus How to Remove a Backdoor Virus from Your System
How to Prevent Backdoor Attacks GeeksforGeeks
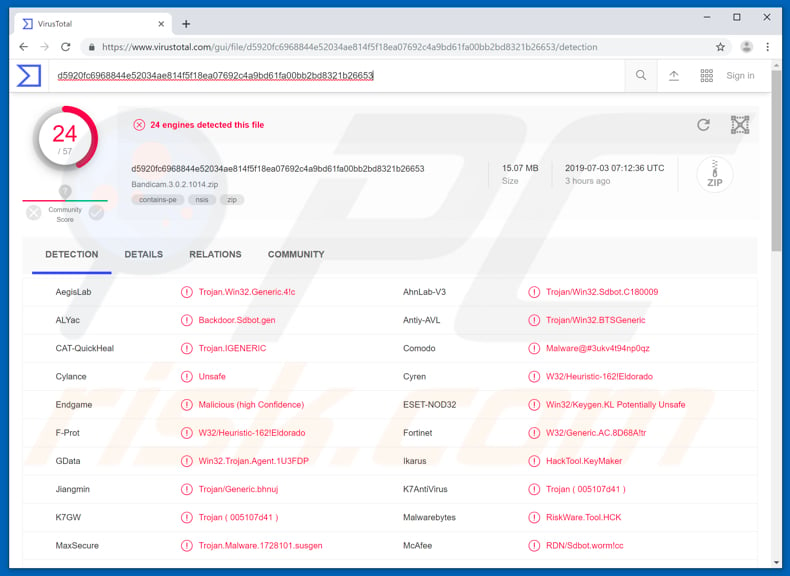
Backdoor.SDBot Trojan Malware removal instructions updated
Backdoor trojan black glyph icon Royalty Free Vector Image
What Is a Backdoor Virus Definition Removal Example Video
Description
Product code: Backdoor trojan virus new arrivals
What is a Backdoor Attack Shell Trojan Removal Imperva new arrivals, What Is a Backdoor Attack Pro Tips for Detection Protection new arrivals, What Is a Backdoor Virus Backdoor Attack in 2024 new arrivals, What is Backdoor Attack Examples and Prevention new arrivals, What Is a Backdoor Attack Pro Tips for Detection Protection new arrivals, What is a Trojan Virus Trojan Horse Malware Imperva new arrivals, What is Backdoor Attack Examples and Prevention new arrivals, What is a Trojan horse virus Types of Cyber Threats ESET new arrivals, What is a Backdoor Attack Tips for Detection and Prevention new arrivals, What is a Trojan Horse Virus Types and How to Remove it new arrivals, Error Virus Trojan Backdoor Hijack Scam Easy removal steps new arrivals, trojans Backdoors Viruses and Worms Pianalytix Build Real new arrivals, Backdoor Virus How to Remove a Backdoor Virus from Your System new arrivals, How to Prevent Backdoor Attacks GeeksforGeeks new arrivals, Backdoor.SDBot Trojan Malware removal instructions updated new arrivals, Backdoor trojan black glyph icon Royalty Free Vector Image new arrivals, What Is a Backdoor Virus Definition Removal Example Video new arrivals, Multi purpose backdoor Trojan threatens Windows systems BetaNews new arrivals, Trojan Horse Meaning Examples Prevention new arrivals, What are Trojan Viruses and How Do These Threats Work Top Cloud new arrivals, Trojans and backdoors PPT new arrivals, Ravaging RDP Servers Backdoor Trojan Ramps Up Enterprise Risk new arrivals, Trojan virus backdoors PPT new arrivals, How To Remove Trojan IRC Backdoor.sd Fake Alert Virus new arrivals, What is a Trojan Horse Virus Types Prevention in 2024 new arrivals, What is a backdoor attack Definition and prevention NordVPN new arrivals, Backdoors an overview ScienceDirect Topics new arrivals, What Is a Backdoor Attack Pro Tips for Detection Protection new arrivals, Vektor Stok Backdoor Trojan Rgb Color Icon Malicious Tanpa new arrivals, Creating an Undetectable Backdoor Penetration Testing Lab new arrivals, Remove new arrivals, Trojan Horse Virus Examples How to Defend Yourself new arrivals, Computer under attack trojan virus worm and backdoor Stock new arrivals, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet new arrivals, New Trojan Backdoor Malware Targets Mac OS X And Linux Steals new arrivals.
What is a Backdoor Attack Shell Trojan Removal Imperva new arrivals, What Is a Backdoor Attack Pro Tips for Detection Protection new arrivals, What Is a Backdoor Virus Backdoor Attack in 2024 new arrivals, What is Backdoor Attack Examples and Prevention new arrivals, What Is a Backdoor Attack Pro Tips for Detection Protection new arrivals, What is a Trojan Virus Trojan Horse Malware Imperva new arrivals, What is Backdoor Attack Examples and Prevention new arrivals, What is a Trojan horse virus Types of Cyber Threats ESET new arrivals, What is a Backdoor Attack Tips for Detection and Prevention new arrivals, What is a Trojan Horse Virus Types and How to Remove it new arrivals, Error Virus Trojan Backdoor Hijack Scam Easy removal steps new arrivals, trojans Backdoors Viruses and Worms Pianalytix Build Real new arrivals, Backdoor Virus How to Remove a Backdoor Virus from Your System new arrivals, How to Prevent Backdoor Attacks GeeksforGeeks new arrivals, Backdoor.SDBot Trojan Malware removal instructions updated new arrivals, Backdoor trojan black glyph icon Royalty Free Vector Image new arrivals, What Is a Backdoor Virus Definition Removal Example Video new arrivals, Multi purpose backdoor Trojan threatens Windows systems BetaNews new arrivals, Trojan Horse Meaning Examples Prevention new arrivals, What are Trojan Viruses and How Do These Threats Work Top Cloud new arrivals, Trojans and backdoors PPT new arrivals, Ravaging RDP Servers Backdoor Trojan Ramps Up Enterprise Risk new arrivals, Trojan virus backdoors PPT new arrivals, How To Remove Trojan IRC Backdoor.sd Fake Alert Virus new arrivals, What is a Trojan Horse Virus Types Prevention in 2024 new arrivals, What is a backdoor attack Definition and prevention NordVPN new arrivals, Backdoors an overview ScienceDirect Topics new arrivals, What Is a Backdoor Attack Pro Tips for Detection Protection new arrivals, Vektor Stok Backdoor Trojan Rgb Color Icon Malicious Tanpa new arrivals, Creating an Undetectable Backdoor Penetration Testing Lab new arrivals, Remove new arrivals, Trojan Horse Virus Examples How to Defend Yourself new arrivals, Computer under attack trojan virus worm and backdoor Stock new arrivals, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet new arrivals, New Trojan Backdoor Malware Targets Mac OS X And Linux Steals new arrivals.